Automated SSL certs for Kubernetes with letsencrypt and cert-manager
Did you ever dream of the day where there would be free TLS certs that were automatically created and renewed when a new service shows up? Well that day has arrived. If you’ve jumped on the cool train and are running Kubernetes in production, then cert-manager is a must have. cert-manager is a service that automatically creates and manages TLS certs in Kubernetes and it is as cool as its sounds.
Here's a kubernetes cert manager tutorial to get things up and running.
Overview to setup cert-manager
To get this setup in a kubernetes cluster, there are 3 main moving pieces:
- the cert-manager service which ensures TLS certs are valid, up to date, and renew them when needed.
- the clusterIssuer resource which defines what Certificate Authority to use
- the certificate resource which defines the certificate that should be created
The following steps assume nginx-ingress controller is running in the kubernetes cluster and there is a way to create DNS records. Additionally, assumes Helm is installed.
Here is a Kubernetescert-manger tutorial to get things up and running in a Kubernetes cluster.
- launch cert-manager from the official helm chart
- create a letsencrypt CA clusterIssuer k8s resource
- launch an app (with an ingress) in the kubernetes cluster to be access at a TLS endpoint.
- create a certificate object that describes how to create a TLS cert for the test app
Details to set up cert-manager
Here are the more detailed steps:
- Deploy the
cert-managerhelm chart. Create the values.yaml file then run:helm-install --name my-release -f cert-manager-values.yaml cert-manager. cert-manager can be configured to automatically provision TLS certificates for Ingress resources via annotations on your Ingresses. This is how I set up cert-manager and therefore, I added a two settings to the values.yaml fileingressShim.defaultIssuerNameandingressShim.defaultIssuerKind. Read more about ingressShim here. See my values file here. - Create the letsencrypt CA cluster issuer. Here I used the letsencrypt staging ACME server just for testing, once this worked, I will switch over to letsencrypt production server. I created the following file by running:
kubectl create -f letsencryp-clusterissuer-staging.yaml.
apiVersion: certmanager.k8s.io/v1alpha1
kind: ClusterIssuer
metadata:
name: letsencrypt-staging
spec:
acme:
# The ACME server URL
server: https://acme-staging.api.letsencrypt.org/directory
# Email address used for ACME registration
email: myemail@gmail.com
# Name of a secret used to store the ACME account private key
privateKeySecretRef:
name: letsencrypt-staging
# Enable the HTTP-01 challenge provider
http01: {}
3. Create a test app configured with TLS. Create the kubernetes manifest files (I created a helm chart here) including a deployment, service, and ingress. The ingress needs annotations that tell cert-manager what CA to use to create TLS certificates. The domainexample-nodejs.mydomain.com must have a DNS record that is configured to send traffic to the nginx ingress controller load balancer.
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: myapp-ingress
annotations:
kubernetes.io/ingress.class: nginx
certmanager.k8s.io/cluster-issuer: letsencrypt-staging
spec:
tls:
- hosts:
- example-nodejs.mydomain.com
secretName: example-nodejs-crt
rules:
- host: example-nodejs.mydomain.com
http:
paths:
- path: /
backend:
serviceName: example-nodejs
servicePort: 8080
4. Create the certificate resource with acme http challenge configured.
apiVersion: certmanager.k8s.io/v1alpha1
kind: Certificate
metadata:
name: example-nodejs-crt
spec:
secretName: example-nodejs-crt
dnsNames:
- example-nodejs.mydomain.com
acme:
config:
- http01:
ingressClass: nginx
domains:
- example-nodejs.mydomain.com
issuerRef:
name: letsencrypt-staging
kind: ClusterIssuerOnce this resource is created, there should be a tls cert that is created. If not, then check the logs of the cert-manger service for errors.
Once all these pieces are setup, you will still get an error when trying to access the app in the browser since the certificate was created with the staging letsencrypt server however this still shows that the cert was successfully created.
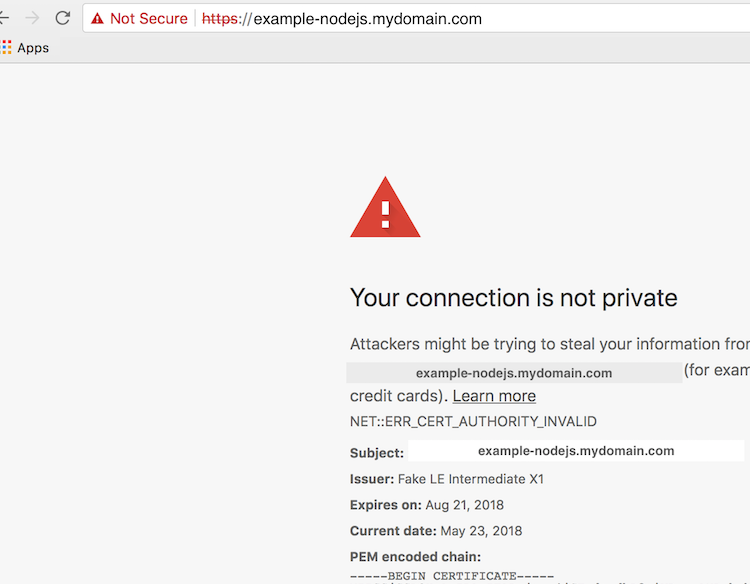
Once this is setup successfully, then create a production cluster-issuer and replace all the references to the letsencrypt-staging clusterissuer with the letsencrypt-prod clusterissuer.
Extra background info for fun if you are interested:
What is letsencrypt? Letsencrypt is a Certificate Authority that issues free TLS certificates. It was launch in 2016 and its purpose is to try to make a safer internet by making it easier and cheaper to use TLS.
What is the ACME protocol? ACME stands for Automated Certificate Management Environment. It is a protocol for automating interactions between certificate authorities and their users’ web servers, allowing the automated deployment of public key infrastructure at very low cost. It was designed by the Internet Security Research Group(ISRG) for their Let’s Encrypt service.
Resources:
- Letsencrypt How It Works
- cert-manager
- my app example and helm charts for this blog post

