Now Available: NSA Hardening Guidance Compliance Report in Fairwinds Insights
The Kubernetes Hardening Guide published by the National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) provides comprehensive guidance to protect Kubernetes systems against security compromises. This guide provides recommendations to help you adopt a strong defense-in-depth approach for your Kubernetes environments. Many of the recommendations in the NSA Kubernetes Hardening Guide can be implemented using Fairwinds Insights. Let’s walk through the latest Insights compliance releases that help you put these best practices in place and harden your Kubernetes clusters.
Achieve NSA and CISA Kubernetes Hardening Guidelines With New Compliance Report
The new NSA Hardening Guidance report consists of checks based on NSA hardening recommendations, making it easy for DevSecOps teams to reduce risk and measure their Kubernetes security posture against industry best practices.
This NSA compliance report also uses automated evidence collection for the majority of checks. The automated checks generate a Pass or Fail result based on data collection and analysis in Insights. In the event of a failed check, the Action Items associated with failed resources highlight where teams should take immediate action.
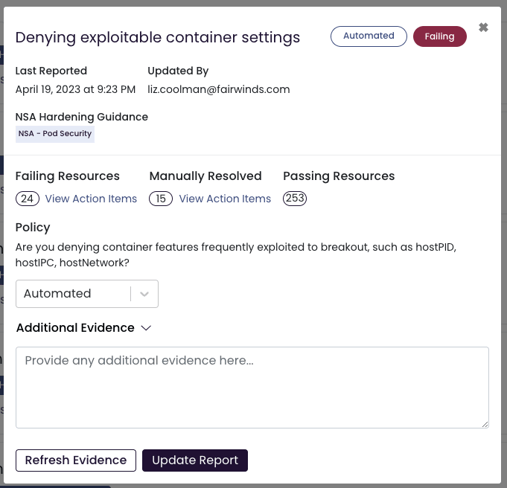
Reach Compliance Faster with Automated Evidence Collection
With automated compliance evidence gathering for many NSA hardening recommendations, you can spend less time reviewing misconfigurations and more time fixing them — and demonstrating good security hygiene. Below are some examples of best practices for Kubernetes hardening that Fairwinds Insights can automate evidence collection of:
-
Pod Security: Use technical controls to enforce minimum levels of security, such as preventing privileged containers, denying container features that are frequently exploited to breakout (hostPID, hostIPC, hostNetwork, allowedHostPath), rejecting containers that execute as the root user (or allow elevation to root), hardening applications against exploitation.
-
Network Separation and Hardening: Use network separation and hardening to control the amount of damage a compromise can cause. This includes:
-
Locking down access to control plane nodes and using separate networks for control plane components and nodes
-
Limiting access to the Kubernetes etcd server (etcd should be managed through the application program interface (API) server)
-
Configuring control plane components to use Transport Layer Security (TLS) certificates to ensure authenticated, encrypted communications
-
Encrypting etcd at rest
-
Putting credentials and sensitive information encrypted in Kubernetes Secrets
-
Authentication and Authorization: Use strong authentication and authorization to limit user and administrator access as well as to limit the attack surface. Make sure that anonymous login is disabled and create role-based access control (RBAC) policies with unique roles for the infrastructure team, service accounts, developers, users, and administrators.
-
Security Policy: Your security policy should require you to periodically review all Kubernetes settings and use vulnerability scans to help ensure risks are appropriately accounted for and security patches are applied. Follow application security best practices, including upgrading as needed, applying security patches and updates in a timely manner, performing vulnerability scans and penetration tests periodically, and removing unused components from the environment.
Try the New NSA Hardening Guidance Compliance Report
The NSA and CISA are continuing to update the Kubernetes hardening guide based on industry feedback and a changing threat landscape. The recommendations for hardening Kubernetes clusters are helpful for organizations, but it can be challenging to keep track of your progress against all your goals in a complex environment like Kubernetes.
This new compliance report in Fairwinds Insights can help you track your progress on hardening your Kubernetes environment in line with NSA and CISA guidance. If you want to see how Insights can help you harden your K8s clusters but you are not currently a Fairwinds Insights customer, try our free tier for environments up to 20 nodes, two clusters, and one repo. (Not sure how to get started? This post that walks you through the simple process.) If you are already a Fairwinds Insights user, log in to the user interface (UI) and click on the Compliance section to get started on your report so you can begin remediating any issues.


